User Defined Routes and Network Virtual Appliances
DISCLAIMER: The information in this guide is provided "as is" without any guarantee of completeness, accuracy, timeliness, or of the results obtained from the use of this information. The author assumes no responsibility for any errors or omissions in the content. It is meant for general information purposes only and should not be used as a substitute for professional advice. The author is not responsible for any damages caused by the use of this information. By using this guide, you agree to hold the author harmless from any and all claims, damages, or expenses that may arise from your use of the information.
Introduction
This document covers services that are actively being used in my Azure lab. Furthermore, this document is to be used as more of a reference or checklist, than a detailed, step-by-step guide. It is assumed that you have basic understanding and know-how of the following Azure services/resources:
- Azure VNet (Virtual Network).
- Azure VNet Peering
- Azure Subnets.
- Azure NSG (Network Security Groups).
- Azure Route Tables.
- Sophos XG Next-Gen Firewall as the NVA (Network Virtual Appliance).
Requirements
- Pending...
Diagrams
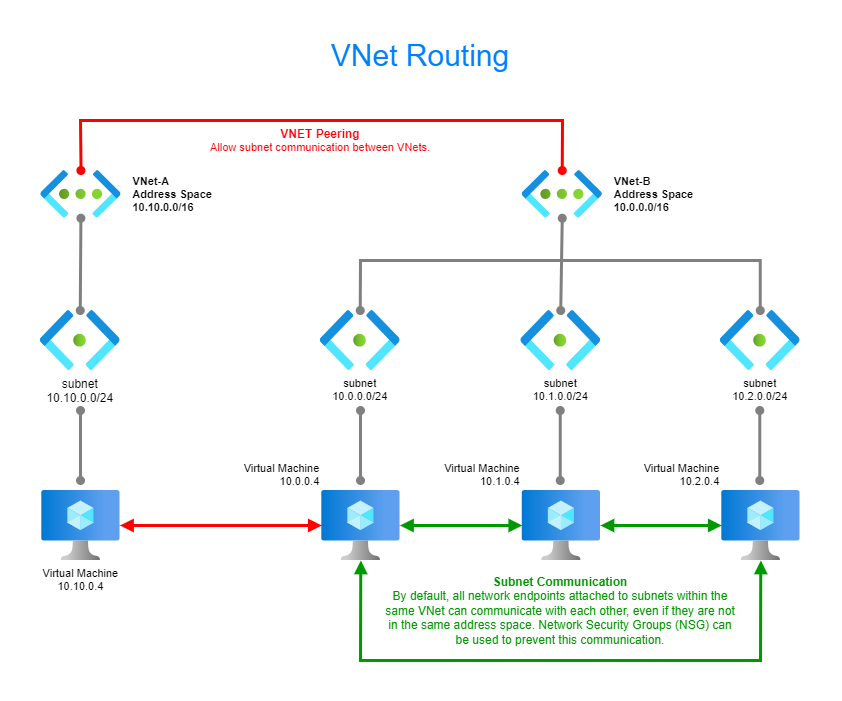
VNet Routing
The diagram presented here utilizes generic VNet names such as VNet-A, VNet-B, etc. It is intended to serve as a study guide for comprehending the connection between Azure Subnet communication and the communication between Azure Subnets and VNets via VNet Peering. In the production network of my Azure lab, Azure VNet Peering and Azure Route Tables are employed to facilitate communication with the Sophos XG Next-Gen Firewall, which resides within a separate VNet.
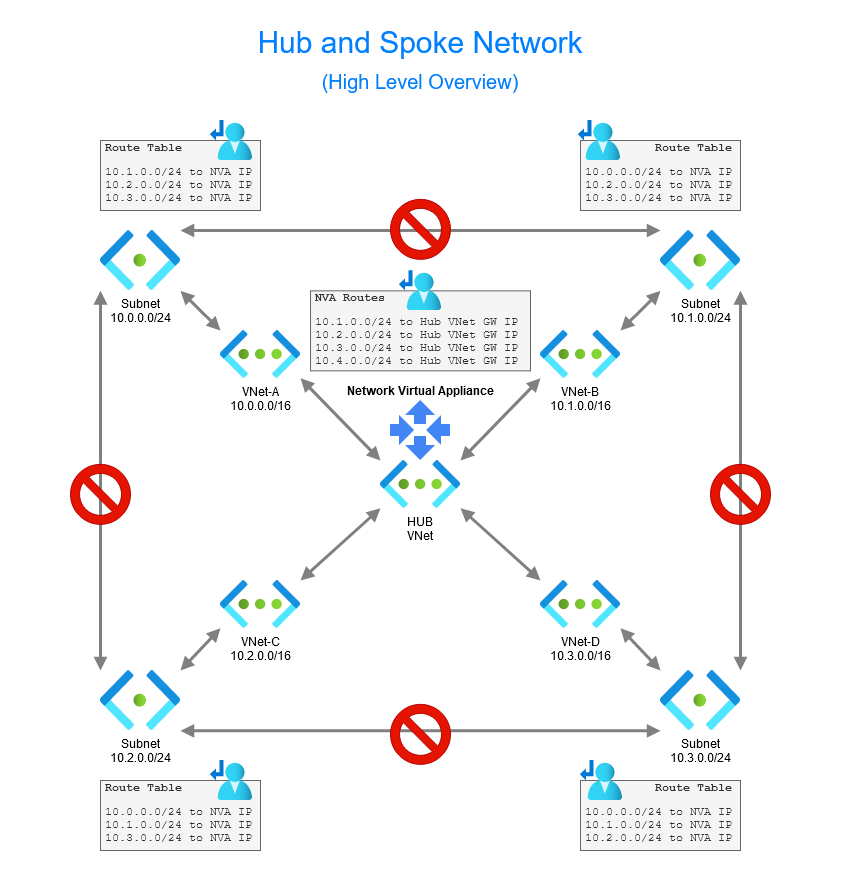
Hub and Spoke Network (High Level Overview)
In this diagram, generic VNet names like VNet-A, VNet-B, etc. are used to depict the scenario. The diagram highlights the significant relationship between VNets when the Sophos XG Next-Gen Firewall is deployed in the "HUB" VNet. By default, the "spoke" VNets cannot directly communicate with each other. To establish connectivity, the spoke VNets utilize Azure VNet Peering to establish connections with the HUB VNet.
To enable traffic routing between VNets, Azure Route Tables are created and configured on each spoke VNet. These route tables are used to direct traffic towards the HUB VNet. In turn, the HUB VNet utilizes a Sophos Static Route table to route traffic to the HUB VNet's gateway IP address. Once the gateway receives the traffic, it possesses the necessary routing information to forward the traffic to other spoke VNets.
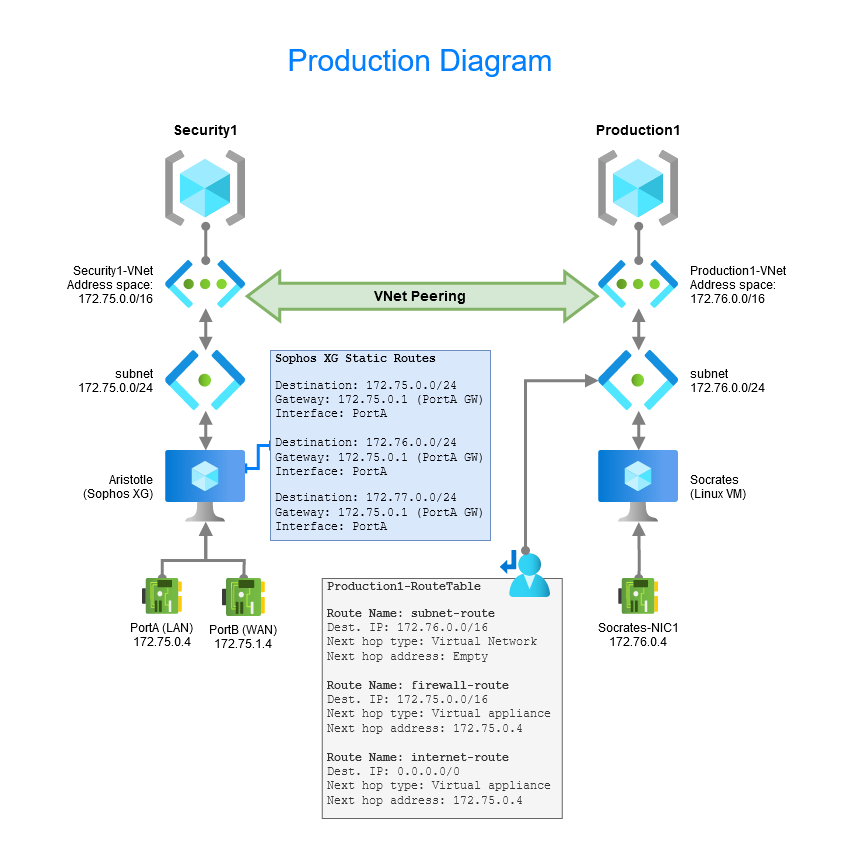
Production Diagram and Notes
The provided production diagram includes the names of all the resources and services currently being utilized in my Azure lab. Please observe the presence of two VNets and the VNet Peering established between them. Additionally, it is important to note the significance of the Sophos XG Static Routes and the production1-routeable for ensuring proper data flow. These routing mechanisms play a crucial role in maintaining the correct flow of data within the network.
Azure Network Configuration
Sophos XG Post Deployment Configuration
Configure Interface Monitoring
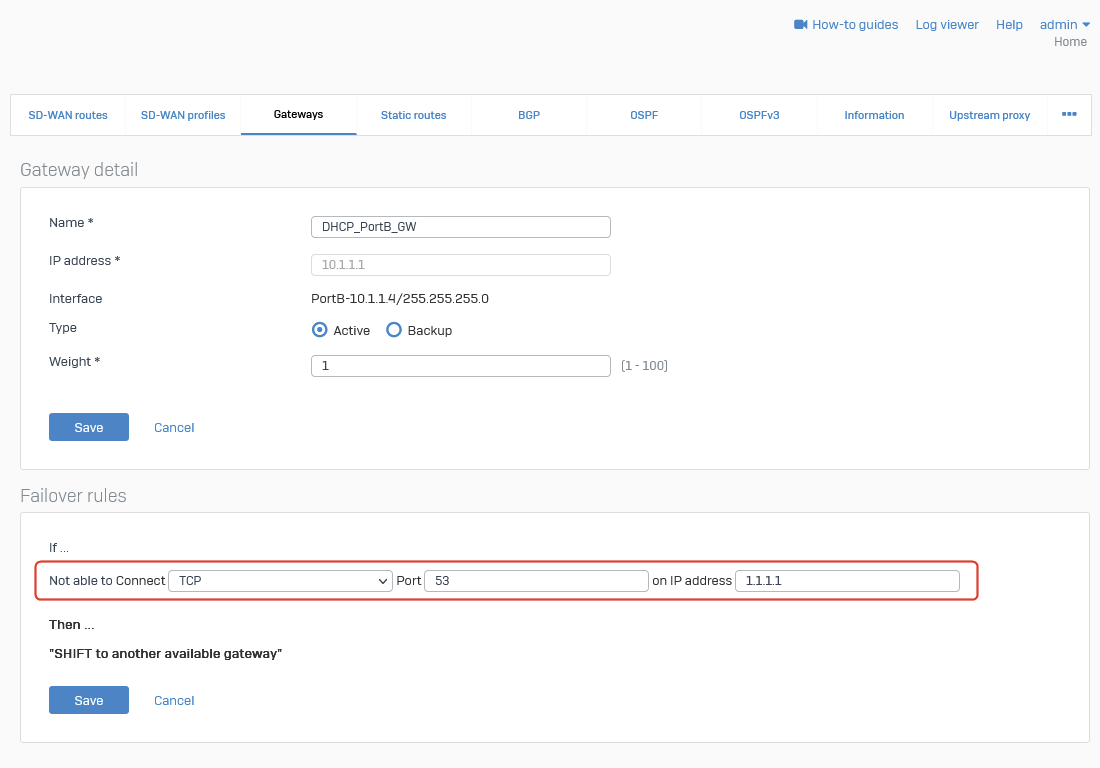
- Navigate to Routing ⮞ Gateways ⮞ Edit DHCP_PortB_GW.
- In the Failover rules section, there should be a single default rule. Click the Edit button.
- Change
PINGtoTCP. - Change Port
*to53. - Change the IP Address to
1.1.1.1. - Save the changes.
Screenshot example:
Configure Static Routes
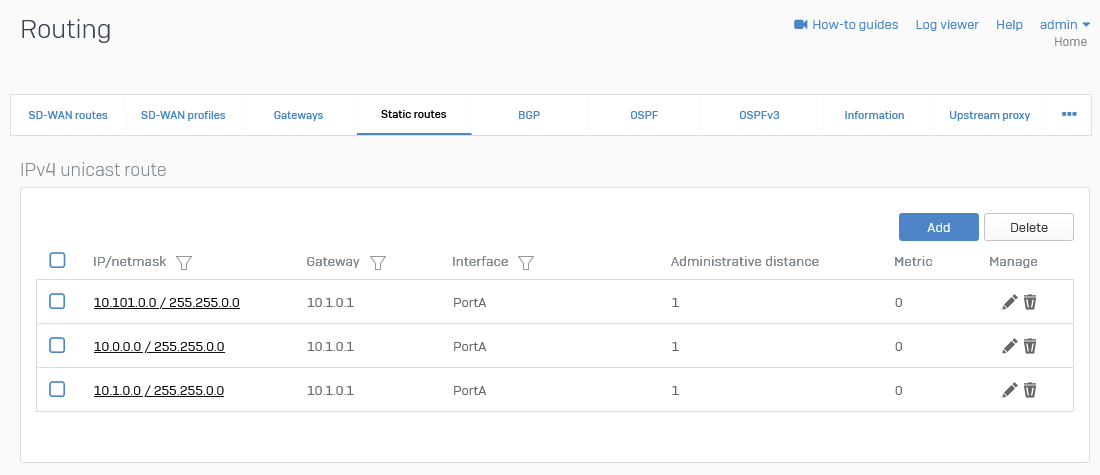
- Navigate to Routing ⮞ Static routes.
- Add an IPV4 unicast route.
Screenshot example:
Configure Services (Ports)
Add Service(s)
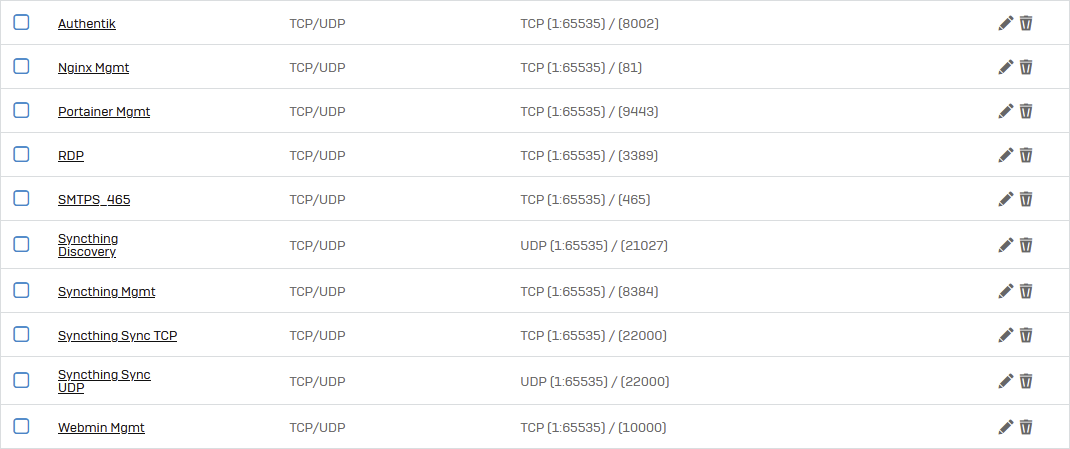
Production Service(s) List
| Name |
Type |
Protocol |
Source port |
Destination port |
| Authentik |
TCP/UDP |
TCP |
1:65535 |
8002 |
| Nginx Mgmt |
TCP/UDP | TCP | 1:65535 | 81 |
| Portainer Mgmt | TCP/UDP | TCP |
1:65535 | 9443 |
| RDP | TCP/UDP | TCP |
1:65535 | 3389 |
| SSH (TCP Only) | TCP/UDP | TCP |
1:65535 | 22 |
| SSH (socrates) | TCP/UDP | TCP |
1:65535 | 2222 |
| Syncthing Discovery | TCP/UDP | UDP |
1:65535 | 21027 |
| Syncthing Mgmt | TCP/UDP | TCP |
1:65535 | 8384 |
| Syncthing Sync TCP | TCP/UDP | TCP |
1:65535 | 22000 |
| Syncthing Sync UDP | TCP/UDP | UDP |
1:65535 | 22000 |
| Webmin Mgmt | TCP/UDP | TCP |
1:65535 | 10000 |
Sreenshot example:
Add IP Host
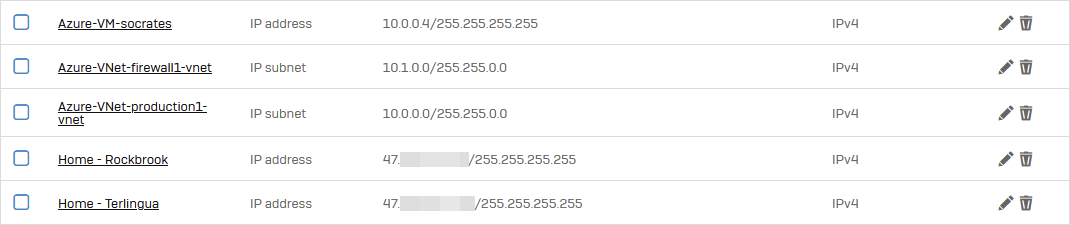
Production Service(s) List
| Name |
IP version |
Type |
IP address |
Subnet |
IP host group |
| Azure-VM-socrates |
IPv4 |
IP address |
10.76.0.4 |
/32 |
|
| Azure-VNetwork-AzureLab1-VNet | IPv4 | IP subnet |
172.75.0.0 |
/16 | Trusted VNets (Azure - Marthur) |
| Azure-VNetwork-Production1-VNet | IPv4 | IP subnet | 172.76.0.0 |
/16 | Trusted VNets (Azure - Marthur) |
| Azure-VNetwork-Security1-VNet | IPv4 |
IP subnet |
172.77.0.0 |
/16 |
Trusted VNets (Azure - Marthur) |
| PortA (LAN) |
IPv4 |
IP address |
172.75.0.4 |
/32 |
|
| PortB (WAN) |
IPv4 |
IP address |
172.75.1.4 |
/32 |
|
| Trusted - Home - Rockbrook | IPv4 | IP address | 47.188.244.16 | /32 |
Trusted WAN |
| Trusted - Home - Terlingua | IPv4 | IP address | 47.188.161.140 | /32 |
Trusted WAN |
| Trusted - Work - Buick | IPv4 | IP address | 208.180.243.26 | /32 | Trusted WAN |
Screenshot example:
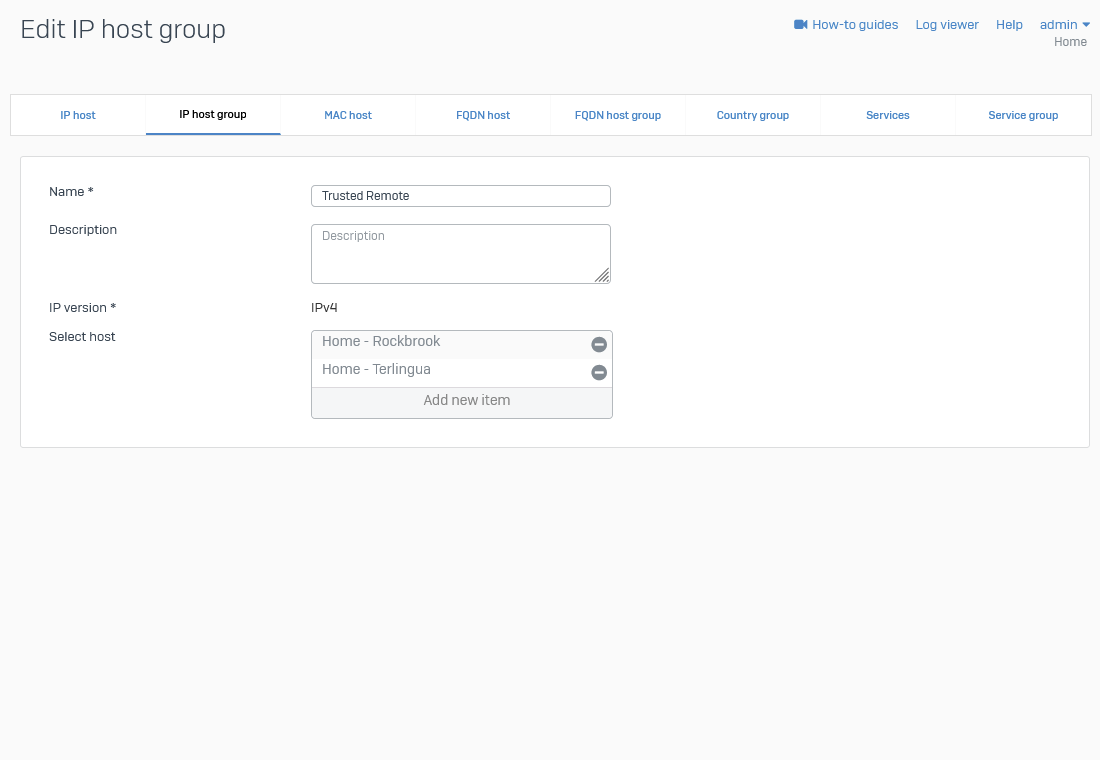
Add IP Host Group
Production Service(s) List
| Name |
Description |
IP version |
Select host |
| Trusted VNets (Azure - Marthur) |
Azure-VNetwork-AzureLab1-VNet Azure-VNetwork-Security1-VNet |
||
| Trusted WAN |
IPv4 |
Trusted - Home - Rockbrook Trusted - Home - Terlingua Trusted - Work - Buick |
Screenshot example:
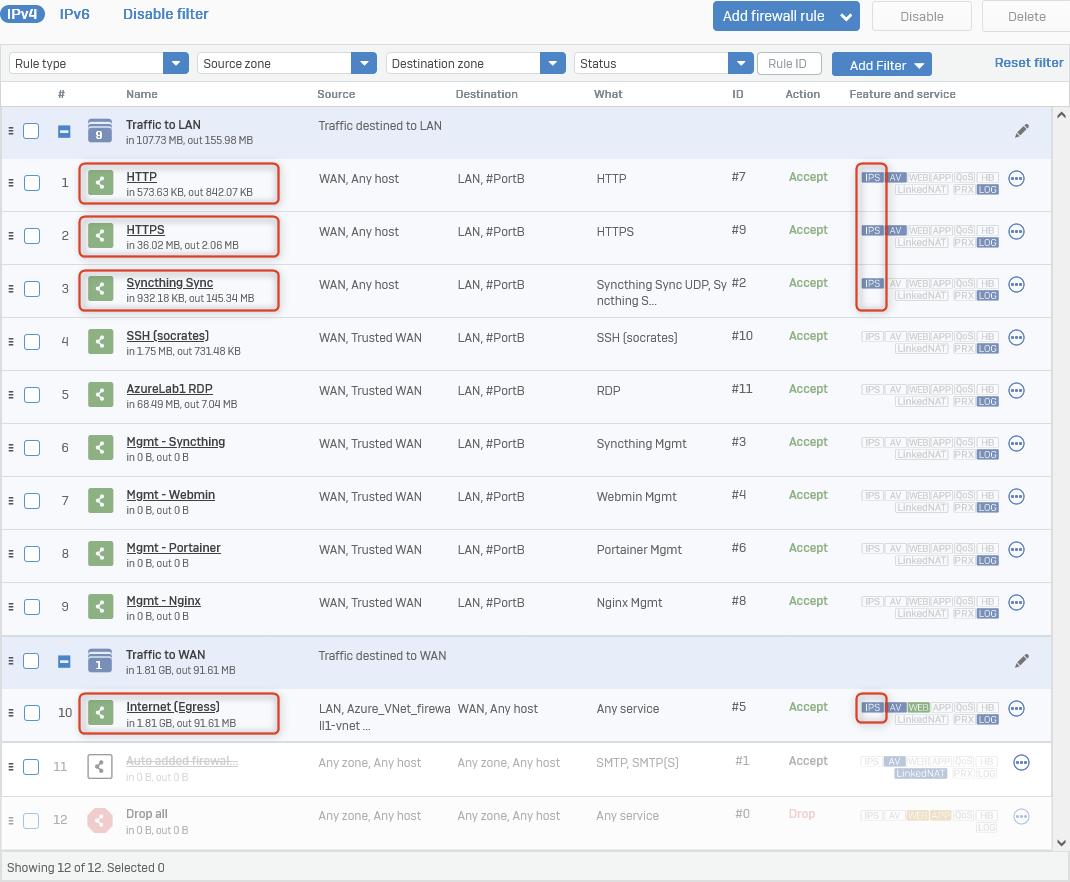
Firewall/DNAT Rules
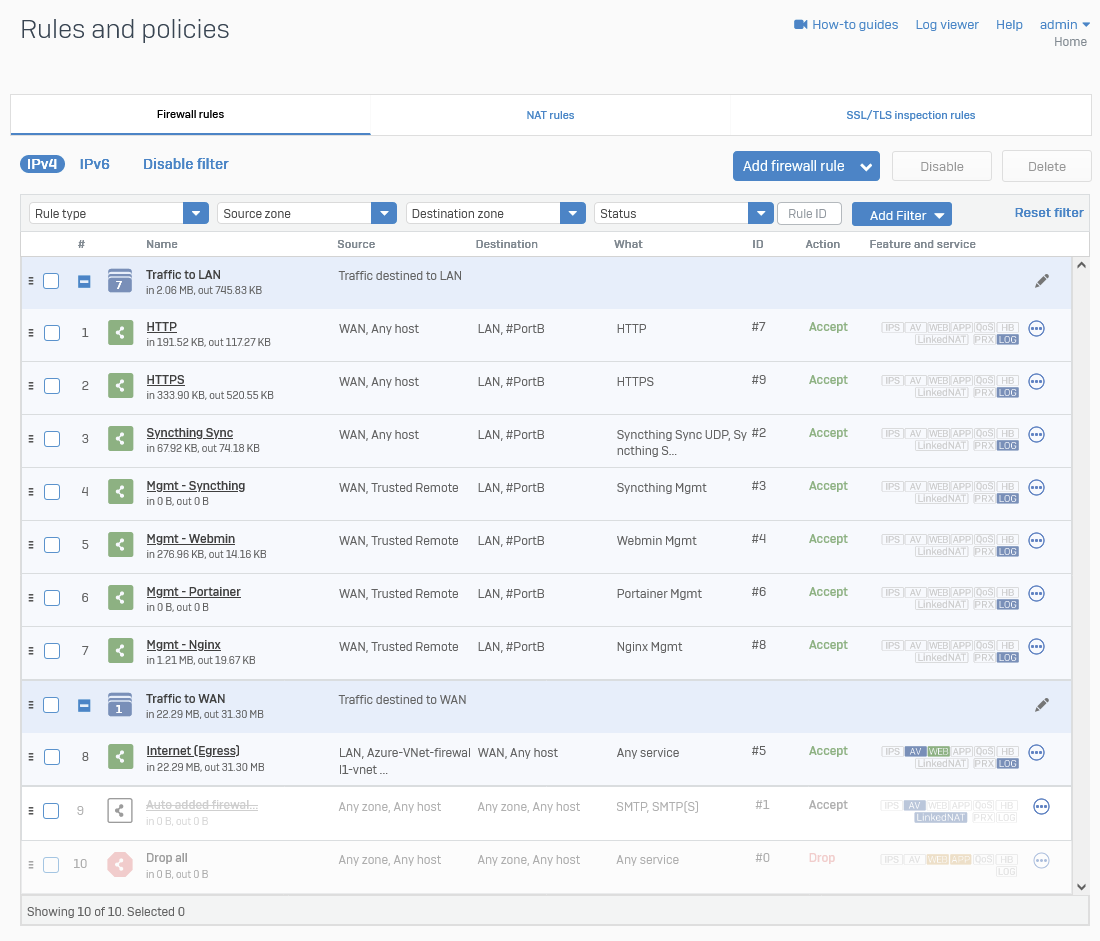
The Traffic to LAN rules were created using the Server access assistant (DNAT) and then the Firewall and Nat rules were cleaned up.
I turned off the "auto added" Firewall and DNAT rule for SMTP/SMTP(S).
Firewall Rules
Screenshot example:
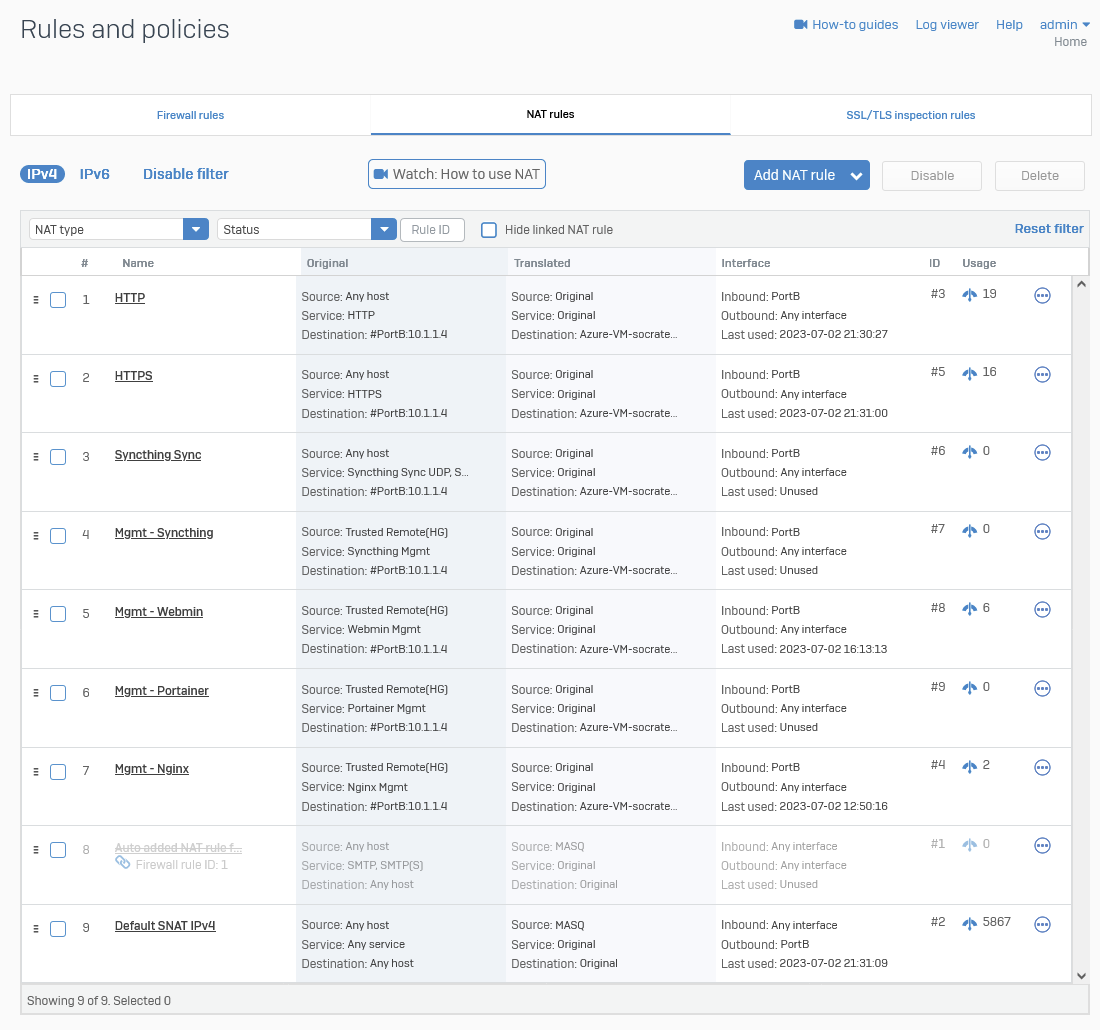
DNAT Rules
Screenshot example:
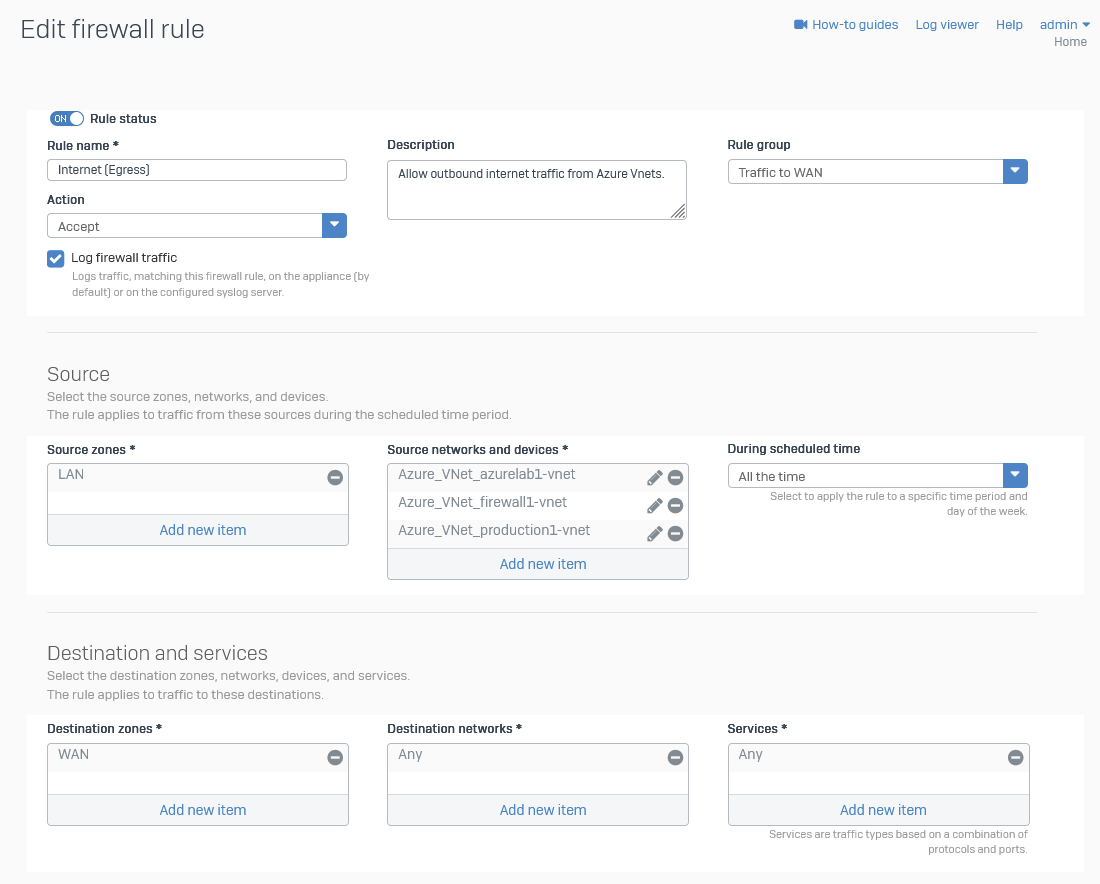
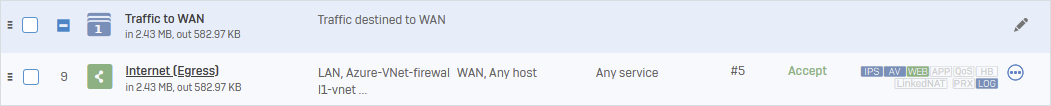
Internet Access (Egress)
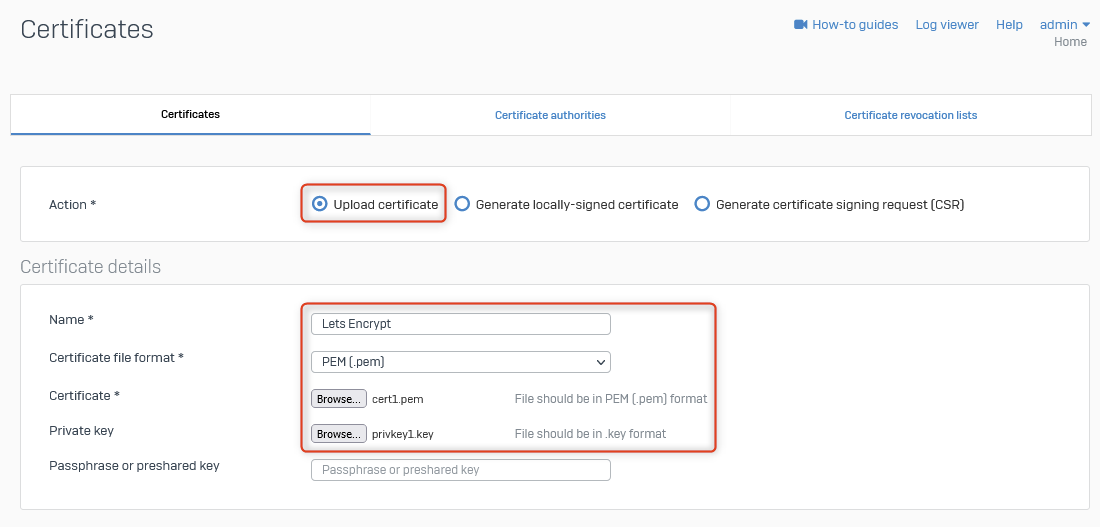
Import/Update Certificates for Sophos WAF
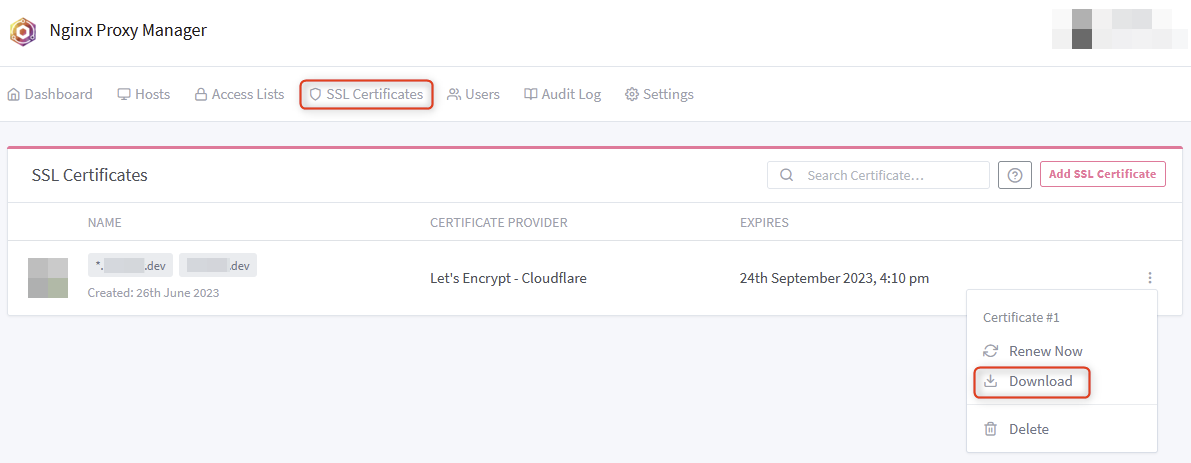
Download Certificate (from Nginx Proxy Manager)
Download the domain related certificates from Nginx Proxy Manager:
- Login to Nginx Proxy Manager (Web GUI).
- Navigate to SSL Certificates.
- Next to the certificate, click on the hamburger/elipses icon and select Download.
- Extract the contents of the zip file.
- Rename
privkey1.pemtoprivkey1.keyrespectively - Sophos requires this change.
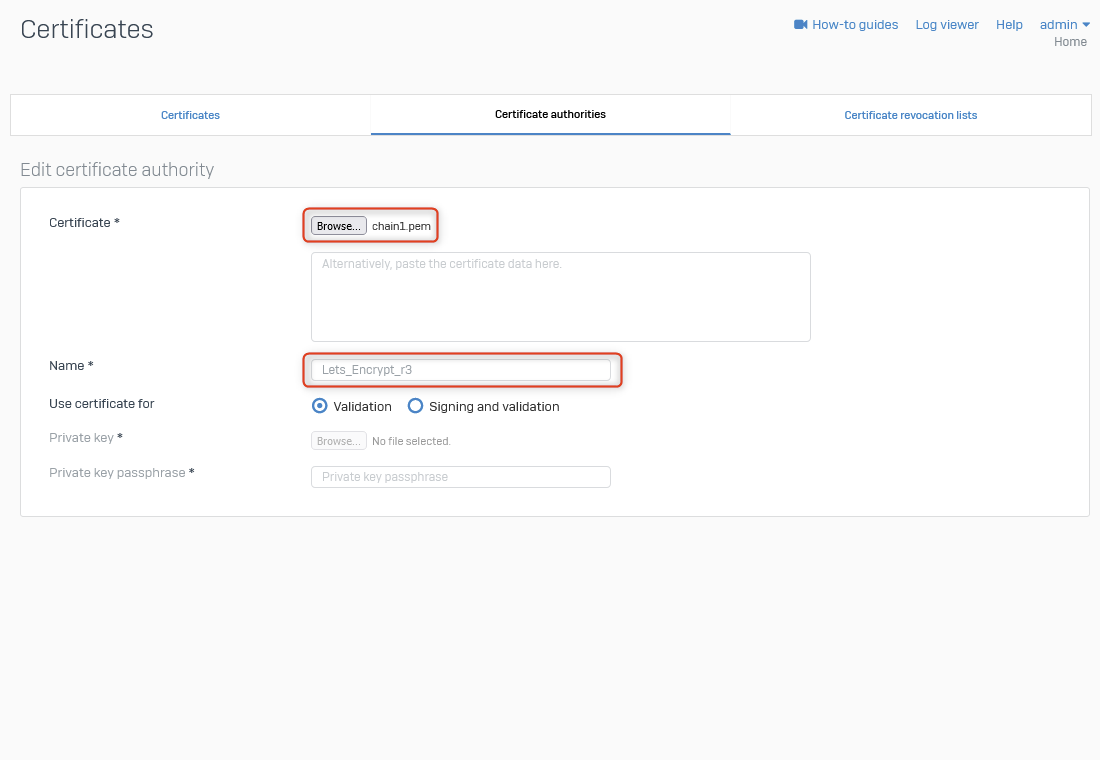
Add/Import the Certificate into Sophos
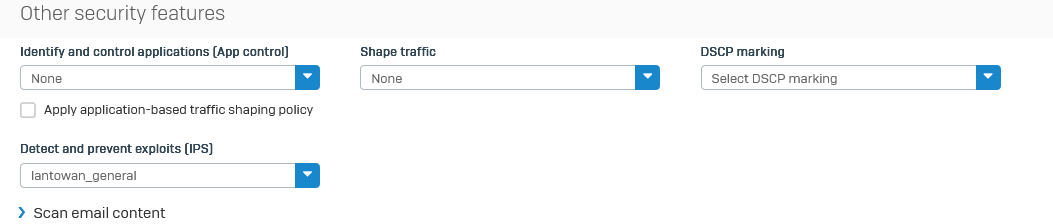
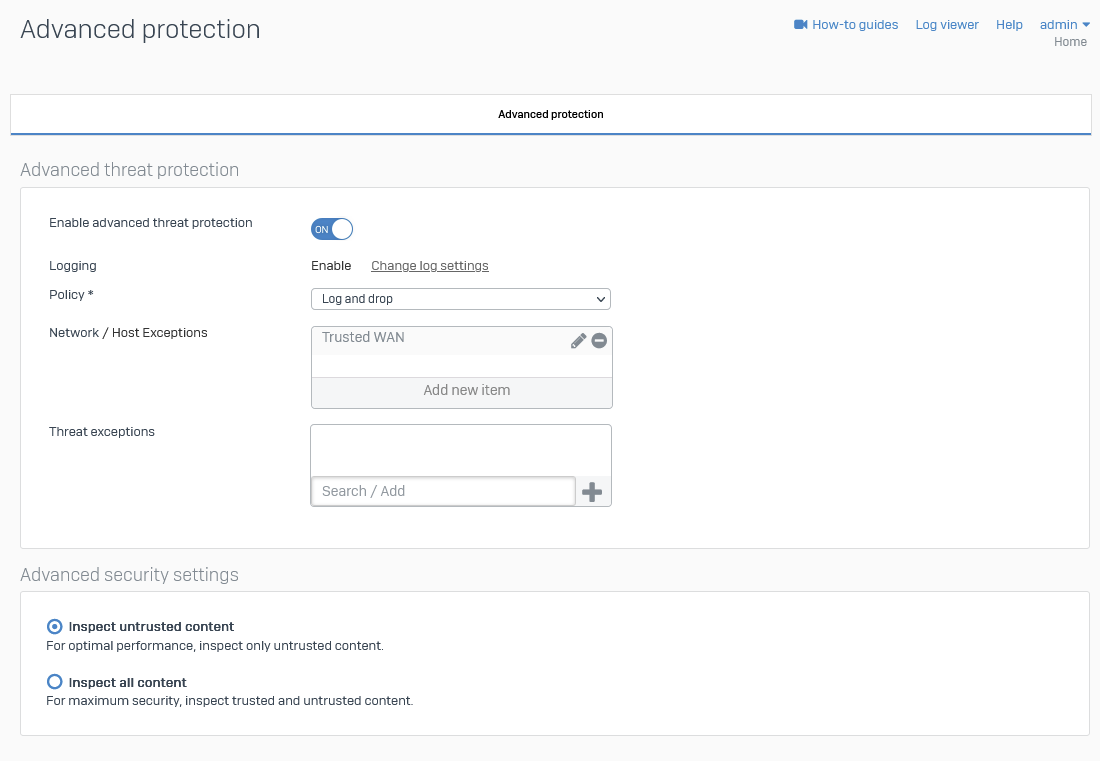
Enable Intrusion Prevention
Enable Advanced Threat Protection
Screenshot example:
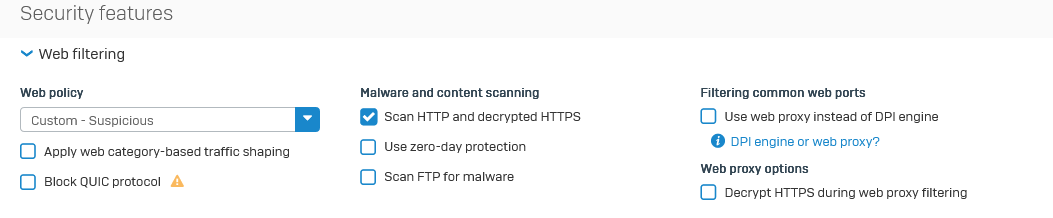
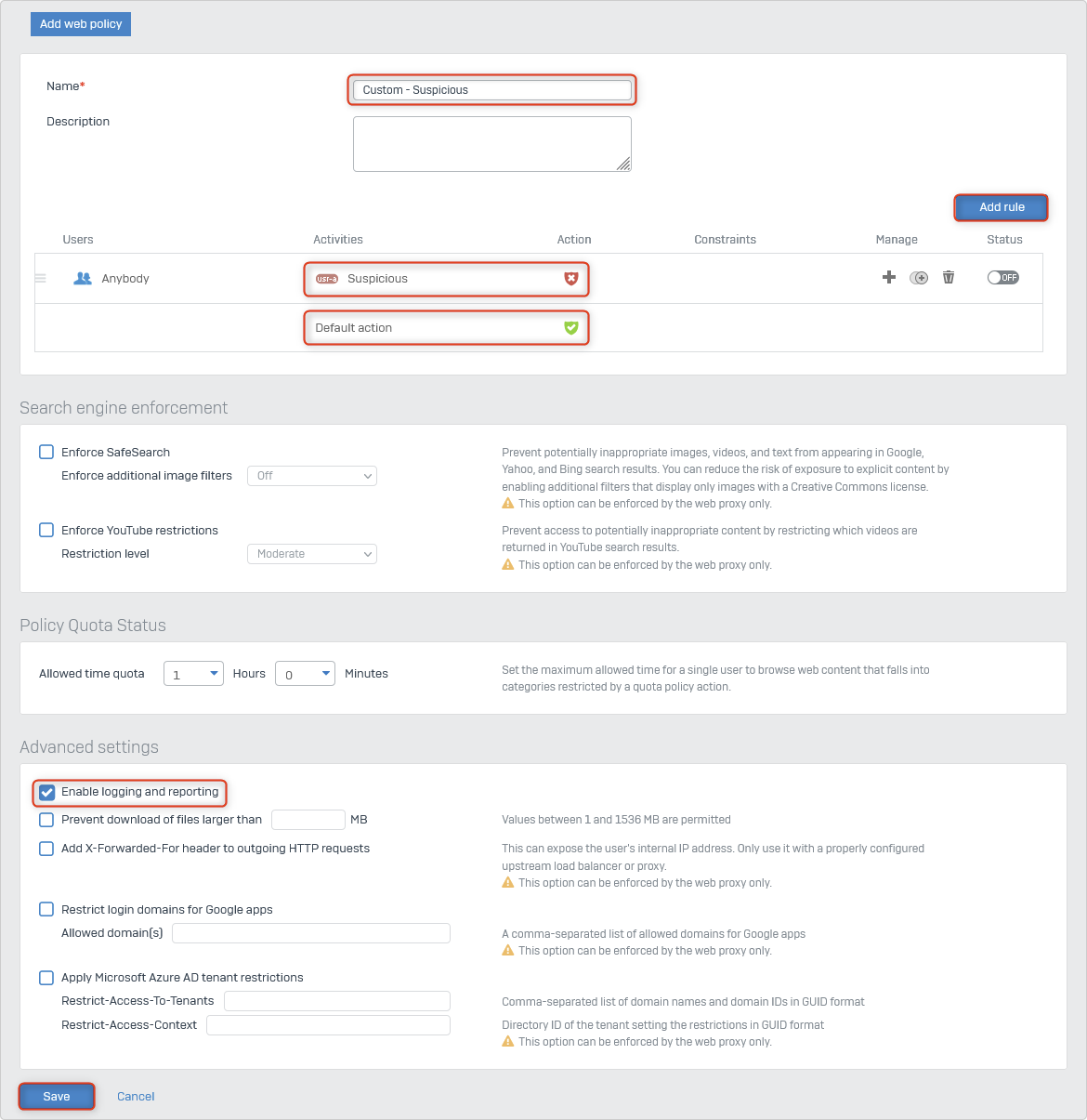
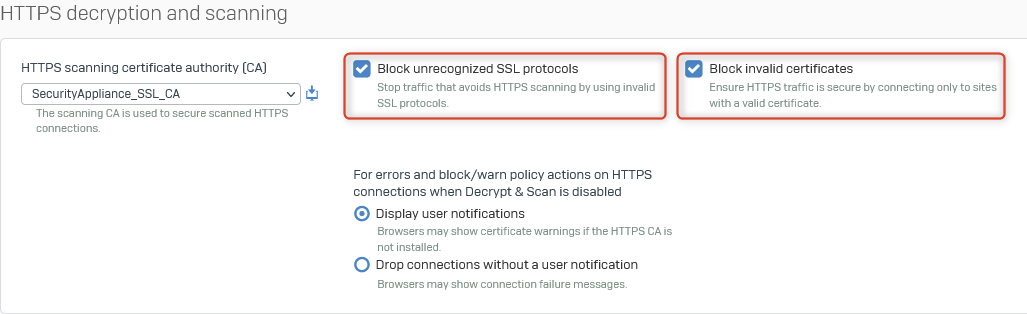
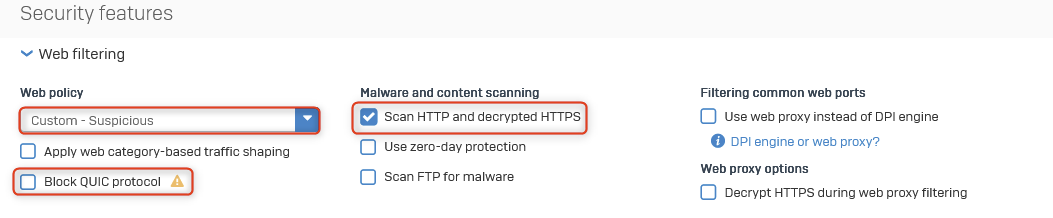
Enable and Configure Web Filtering
Create a Custom Web Policy
Azure Routing Tables
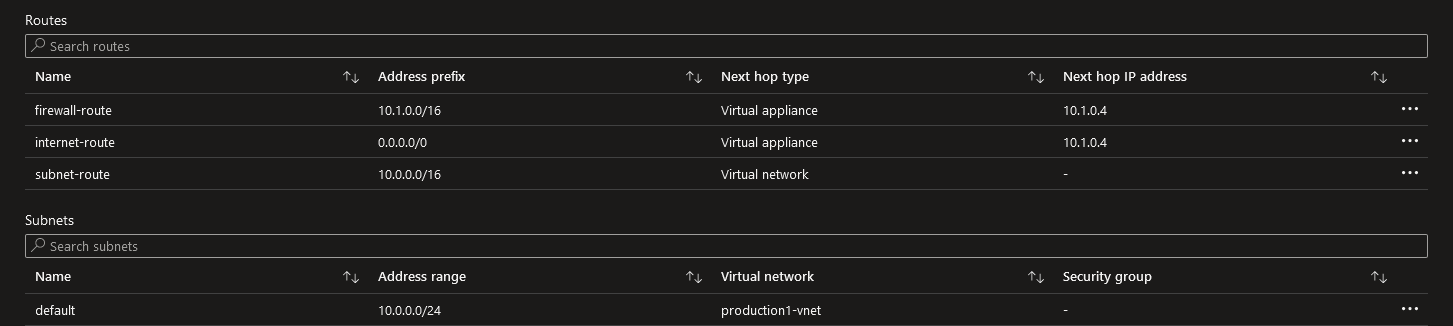
production1-routetable screenshot:
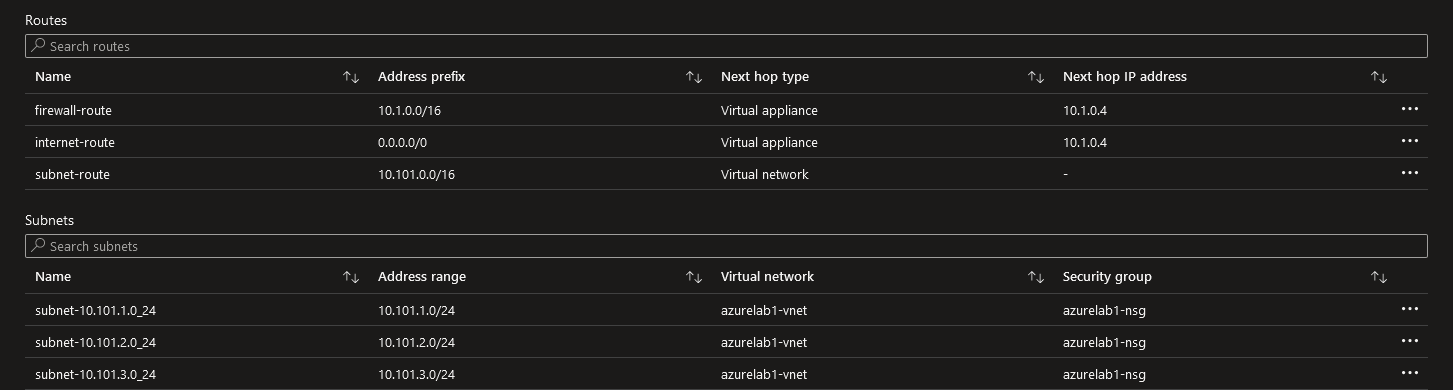
azurelab1-routetable screenshot:
Azure Network Security Groups
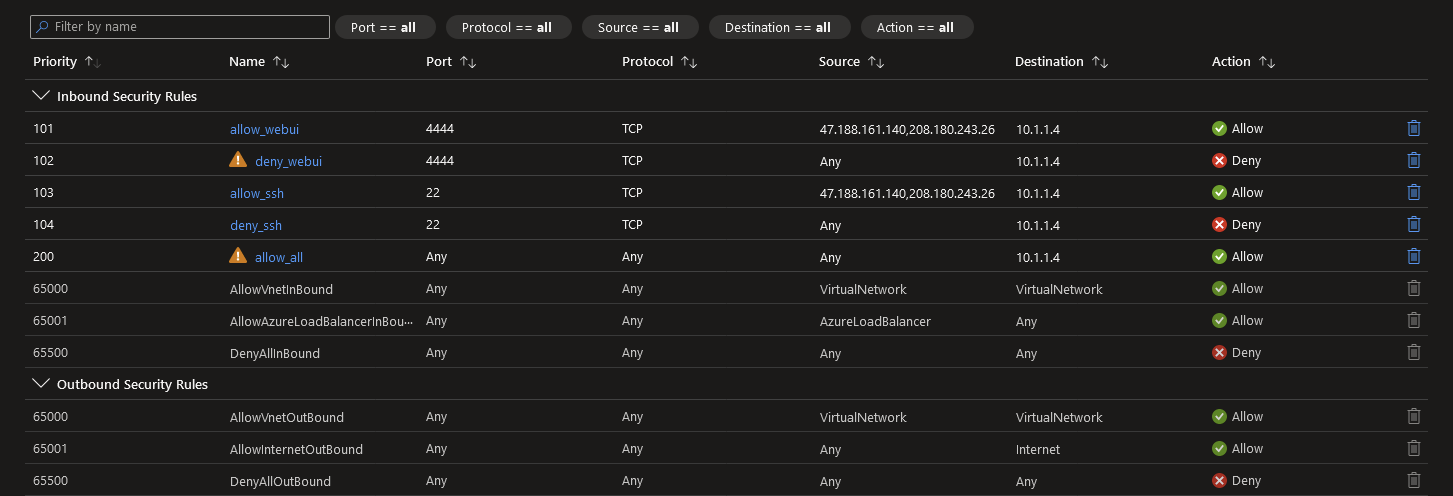
SecurityGroup (Sophos Firewall):
Pending Documentation
Add Sophos Cert to VMs for Decryption.
Azure NSG for both VNets.
Azure Disable Public IP on Spoke VNet.
Cloudflare DNS DNS Only/Proxied configuration.
Nginx Proxy Manager Gotchas w/ Azure VMs.
Sources
- N/A
KB Change/Issue Log
yyyy/mm/dd - Title
Issue
N/A
Solution
N/A
KB Meta
| Page Includes | @9#bkmrk-callout-danger-NoResponsibilityDisclaimer-5wod5ufe |