AppRiver ETP Google Workspace Configuration
Introduction
This is a companion guide to AppRiver ETP Setup and Configuration.
The AppRiver ETP service is handled differently than our typical setup (e.g., Microsoft Office 365), as does the routing of internal Google Workspace messages. Please follow the instructions below to ensure mail is delivered correctly.
Requirements
- Administrative access to AppRiver.
- Administrative access to customers Public DNS.
- Administrative access to customers Google Workspace.
CNAME Record for Mail Relay
This part of the guide requires access/changes to the customers public DNS server (e.g., GoDaddy, Cloudflare, etc.) - specifically the addition of a CNAME record. The CNAME record is utilized after messages are filtered by AppRiver ETP. This step will not change the flow of messages, until the new CNAME is added to the AppRiver ETP configuration.
With our Email Threat Protection service, a special setup for your domain can help ensure that email delivery is kept at a consistent rate for clients utilizing hosted mail with another provider. In the past, we have had issues delivering to the other hosting provider’s MX records (such as G Suite or Rackspace). Other hosting providers can think we are bulk mailing and greylist our servers, resulting in delays for our customers. In order to avoid this from happening, we suggest creating a CNAME DNS record that points to the MX records for your mail host. The extra DNS resolution avoids any delivery issues we have seen in the past when delivering to MX records. We create CNAME records because if your mail host ever changes their delivery locations, the CNAME record will automatically resolve those changes. Once the CNAME is created, we will use that record as the Email Threat Protection delivery location.
- support.zixcorp.com (https://support.zixcorp.com/app/answers/detail/a_id/945)Archived: https://web.archive.org/web/20221102134415/https://support.zixcorp.com/app/answers/detail/a_id/945
The following CNAME DNS Record information may be added to the customers publics DNS (e.g., GoDaddy, Cloudflare, etc.):
| Record Type | Host | Point to (Target) | TTL |
| CNAME | delivery | aspmx.l.google.com | 3600 |
- Record Type - CNAME
- Host - Can be whatever the client prefers, but to make things simple, we usually suggest “Delivery”. (This does not matter, as long as it’s not going to interfere with any other active CNAME records, such as Autodiscover)
- Points to - your hosting provider’s MX record
- TTL - Time to live (TTL) or hop limit is a mechanism which limits the lifespan or lifetime of data in a computer or network.
NOTE: If the "mail" CNAME is already taken, any CNAME will suffice, such as mail1, mail2, etc.
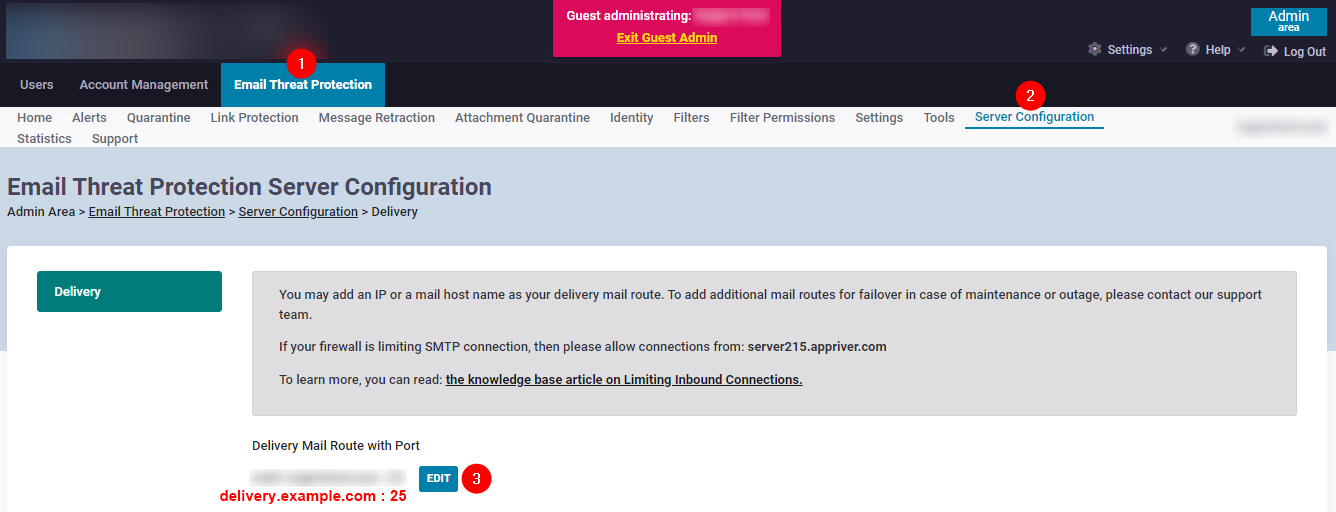
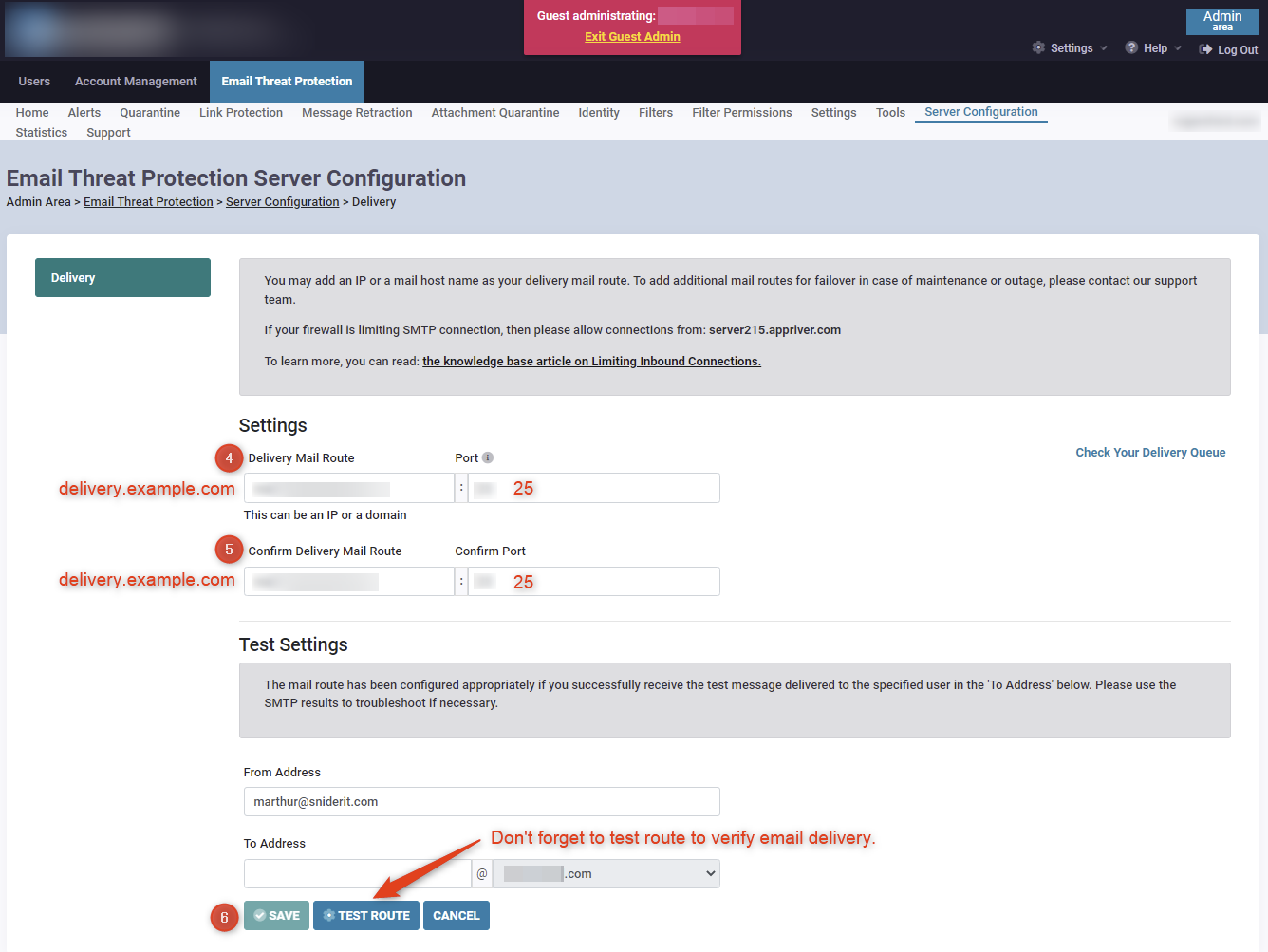
Once the CNAME has been created it will need to be added to the following section under the customers Guest Admin area. The existing entry can be edited to add the new email delivery address. In addition, the new delivery address can be tested as well within the edit page.
Allow Inbound Traffic for AppRiver ETP
This part of the guide requires administrative access to the customers Google Workspace account.
Since AppRiver will be filtering/scanning all inbound traffic for spam/malware content, we can "assume" that all messages being passed on to Google Workspace is clean.
Please use the Google KB article below to configure Google Workspace to allow all traffic sent to it from AppRiver ETP IP Whitelist.
Google KB: Set up an inbound mail gateway
AppRiver ETP IP Whitelist
- 5.152.184.128/25
- 5.152.185.128/26
- 5.152.188.0/24
- 8.19.118.0/24
- 8.31.233.0/24
- 69.20.58.224/28
- 69.25.26.128/26
- 74.203.185.12/32
- 199.30.235.11/32
- 199.187.164.0/24
- 199.187.165.0/24
- 199.187.166.0/24
- 199.187.167.0/24
- 204.232.250.0/24
SOURCE: How do I allow inbound mail from Email Threat Protection in Office 365? - support.zixcorp.com
Avoiding False Positives for Internal Traffic
Complete the following configurations to ensure that internal G Suite traffic will stay internal to G Suite and will not come through the AppRiver ETP service.
Configure Host
-
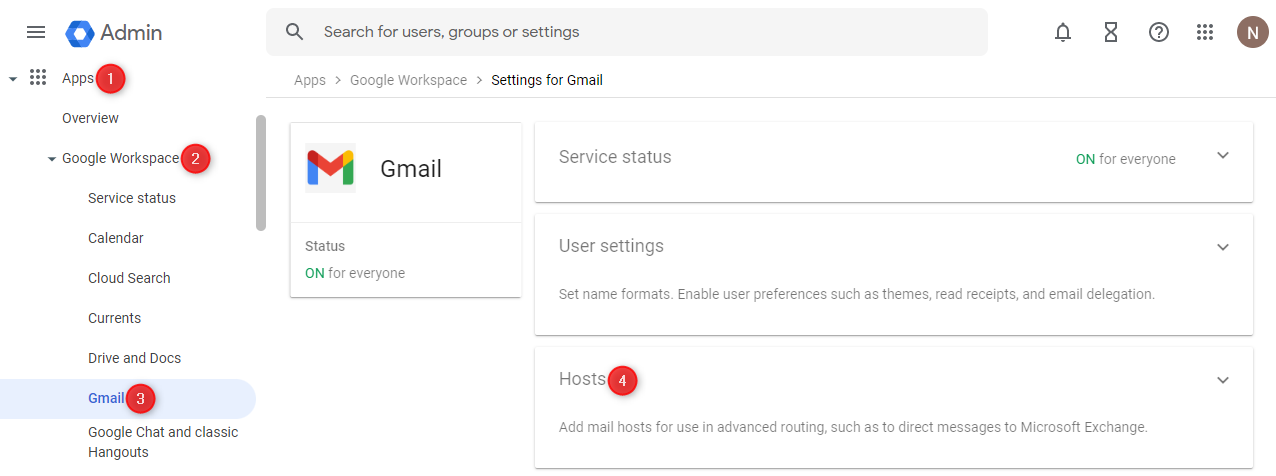
Sign-In to the Google Admin console (https://admin.google.com/).
-
From the dashboard go to Apps > Google Workspace > Gmail.
-
In the right-pane, click on Hosts.
-
Click on ADD ROUTE.
-
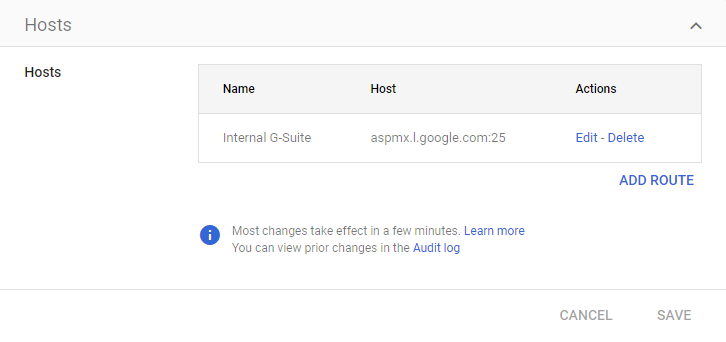
For Name, put
Internal G-Suite, for Single host, enteraspmx.l.google.comand port25(SMTP). -
Do NOT check the following:
- Perform MX lookup on host
Check the following:
- Require mail to be transmitted via a secure (TLS) connection (Recommended)
- Require CA signed certificate (Recommended)
- Validate certificate hostname (Recommended) -
Click on Save.
See example below: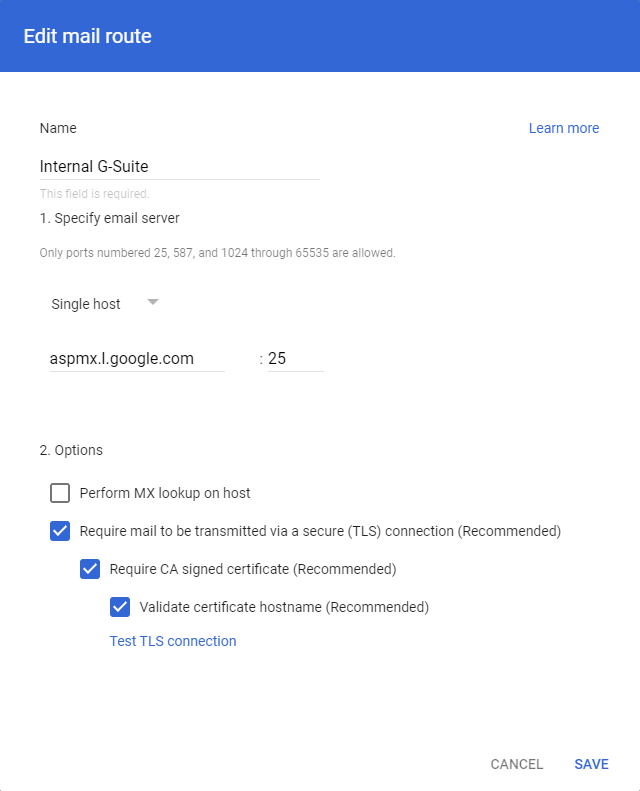
The following settings should now be configured:
Configure Routing
- After completing the Host Configuration, click Settings for Gmail in the top left.
- In the right-pane, click on Routing.
- Enter
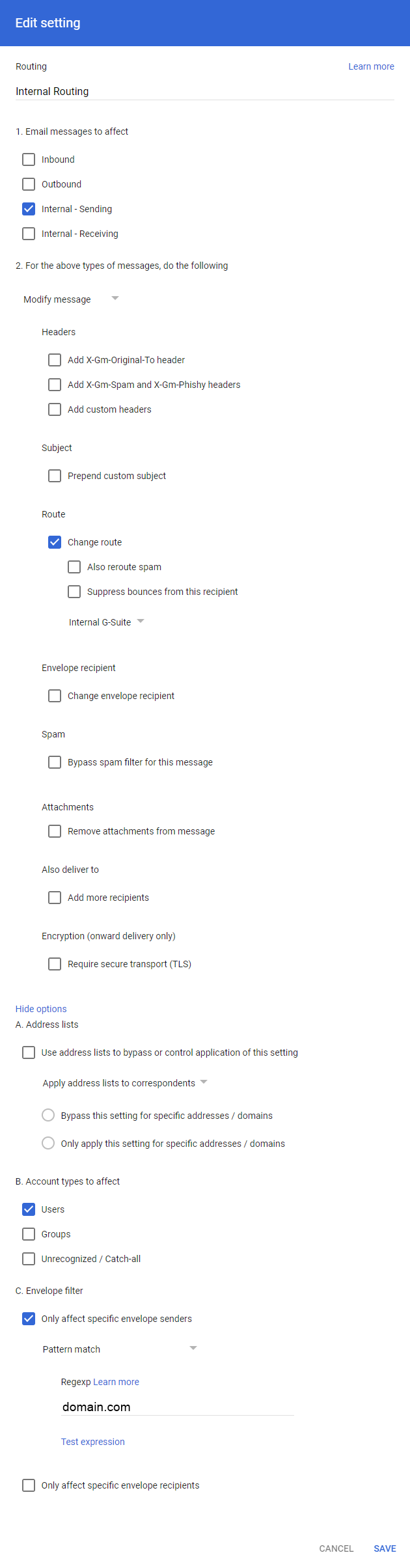
Internal Routingfor the rule name. - Check the following:
Email messages to affect > Internal - Sending (check this box)
Route > Change route (check this box). Afterwards, select "Internal G-Suite" from the dropdown box.
B. Account types to affect > Users (check this box)
C. Envelope filter > Only affect specific envelope senders (check this box) - Enter the customer's domain (e.g., domain.com).
- Click on Save.
See example below:
Sources
- Addressing Third-Party Hosting Mail Delays with Email Threat Protection - support.zixcorp.com
- How do I allow inbound mail from Email Threat Protection in Office 365? - support.zixcorp.com
- Set up an inbound mail gateway - support.google.com
KB Change/Issue Log
yyyy/mm/dd - Title
Issue
N/A
Solution
N/A
KB Meta
| Page Includes |