DC Authoritative (D4) Restore for DFSR
DISCLAIMER: The information in this guide is provided "as is" without any guarantee of completeness, accuracy, timeliness, or of the results obtained from the use of this information. The author assumes no responsibility for any errors or omissions in the content. It is meant for general information purposes only and should not be used as a substitute for professional advice. The author is not responsible for any damages caused by the use of this information. By using this guide, you agree to hold the author harmless from any and all claims, damages, or expenses that may arise from your use of the information.
Introduction
An authoritative (D4) restore is sometimes also referred to as an authoritative (D4) synchronization. This procedure is for performing an authoritative restore with a multiple domain controller environment.
IN A SINGLE DOMAIN CONTROLLER ENVIRONMENT, DO NOT PERFORM THIS PROCEDURE.
There are 2 type of restore modes for Microsoft Windows Domain Controllers:
It's important to note that you should only perform a non-authoritative restore on a secondary (non-authoritative) domain controller, as making changes to the primary domain controller (PDC) can have unintended consequences. Additionally, it's recommended to test the restore process in a non-production environment before performing it in a production environment
Requirements
- Domain Controller environment is using DFSR.
Instructions
- On the Primary Domain Controller (PDC), which is generally considered having the most up-to-date Sysvol copy, launch
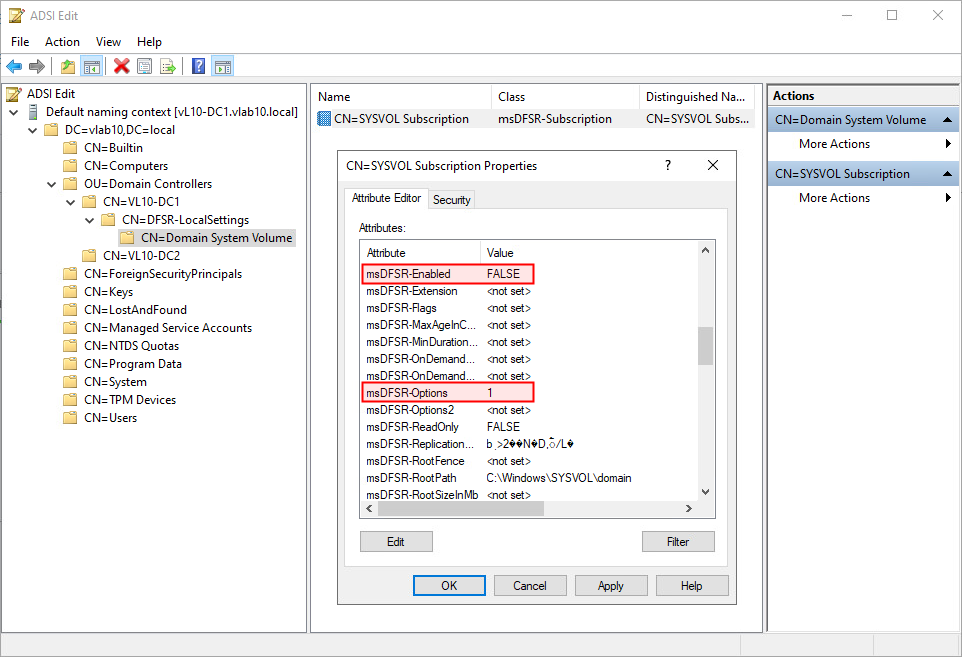
ADSIEDIT.MSCtool and connect toDefault Naming Context. - Browse to
DC=<domain>,DC=local⮞OU=Domain Controllers⮞CN=<PDC NAME>⮞CN=DFSR-LocalSettings⮞Domain System Volume⮞SYSVOL Subscription.
msDFSR-Enabled FALSE msDFSR-options 1
Setting attribute
msDFSR-Optionsto1sets the server to authoritative for the DFSR SYSVOL replicated folder (Primary Copy). - On all other (non-authoritative) domain controllers, set the attribute value:
msDFSR-Enabled FALSE - On all the Domain Controllers, force Active Directory replication throughout the domain:
repadmin /syncallAlternatively, run on the Primary Domain Controller to push synchronization:
repadmin /syncall /APedThe
/APedswitch pushes changes to all domain controllers from the domain controller executing the command. Without this switch, the default action is to pull updates, which is why msDFSR-options=1 is required when not using the/APedswitch. - On all Domain Controllers, starting with the Primary Domain Controller, run the following command from an elevated command prompt:
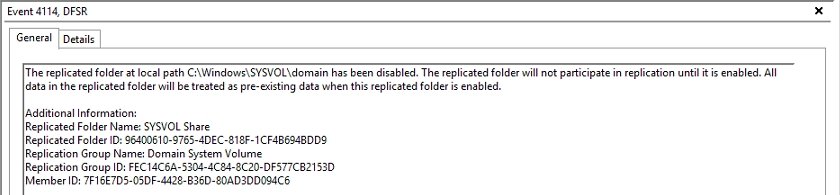
DFSRDIAG POLLADThis command will immediately poll AD for configuration changes on the DC.
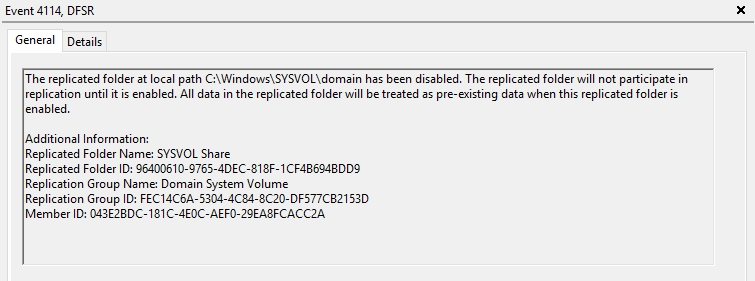
On the same server, You will see Event ID 4114 in the DFSR event log indicating SYSVOL is no longer being replicated on the PDC.
If
DFSRDIAGdoes not exist, run the following PowerShell command to install the DFS Management Tools:Add-WindowsFeature RSAT-DFS-Mgmt-Con
Alternatively, DFS Management Tools can be installed from the Add Roles and Features Wizard:
- On all domain controllers, stop (and disable) the DFSR service.
This step is required so that DC will stop communicating with DFSR Sysvol database and cannot make changes or modifications to DFSR configuration. This step is not given in original MS KB article.
- On the Primary Domain Controller (PDC), start (and enable) the DFSR service.
- On Primary Domain Controller (PDC), change the attribute value for
msDFSR-Enabledback toTRUE(step 2).
msDFSR-Enabled TRUE This will ensure that this PDC server is the primary member for DFSR replicated folder. This will also resume DFSR replication on the PDC server only; DFSR replication on other DCs is still disabled.
This step also resets msDFSR-options to 0 from 1 automatically (we set it to 1 in Step 1), which means DFSR Sysvol authoritative restore is attempted on this DC (PDC).
Note that while you will have enabled DFSR replication on this DC (PDC) authoritatively, you must ensure that the DFSR service has been stopped on other DCs and that DFSR replication is in the disabled state. Otherwise, it leads to DFSR database conflicts and issues.
- On all Domain Controllers, force Active Directory replication throughout the domain:
repadmin /syncall - On the Primary Domain Controller (PDC), run the following command from an elevated command prompt:
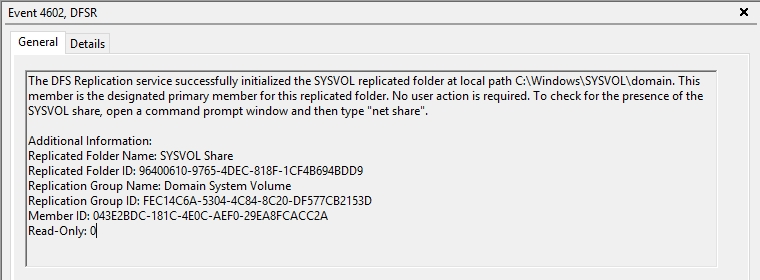
DFSRDIAG POLLADCommand Output should show Sysvol and Netlogon shares (Active Directory logon shares), it means Sysvol is fully initialized and designated as primary member for Sysvol replication.
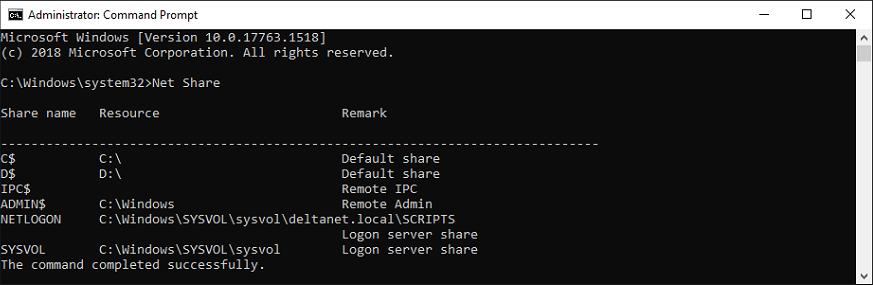
This command will poll the configuration changes in AD immediately for that DC with reference to DFSR. On the same server, you will see Event ID 4602 in the DFSR event log indicating SYSVOL has been initialized. That domain controller (PDC) has now done a “D4” of SYSVOL successfully. Open command prompt and type:
Net Share - Start (and enable) the DFSR service on the other non-authoritative DC servers one-by-one. On these servers, verify Event ID 4114 in the DFSR event log indicating SYSVOL is no longer being replicated on each of them. Starting the DFSR service will enable these DCs to start accessing DFSR configuration database; however, DFSR replication is still not enabled.
- On all other (non-authoritative) Domain Controllers, one-by-one, set the attribute value for
msDFSR-Enabledback toTRUE(step 2):
msDFSR-Enabled TRUE This step will enable DFSR replication across the domain controllers and they will start non-authoritatively restoring DFSR Sysvol
- On all Domain Controllers, force Active Directory replication throughout the domain:
repadmin /syncall - On all other (non-authoritative) Domain Controllers, one-by-one, run the following command from an elevated command prompt:
DFSRDIAG POLLADOn the non-authoritative DC servers, you will see Event ID 4604 in the DFSR event log indicating SYSVOL is now initialized and replicating correctly on each of them. These domain controllers have now done a “D4” of SYSVOL successfully.
Open command prompt and run:
Command Output should show SYSVOL and Netlogon shares (Active Directory logon shares), it means SYSVOL is fully initialized and synchronized with a primary replication partner.Net Share
Sources
- rebeladmin.com - Non-Authoritative and Authoritative SYSVOL Restore (DFS Replication)
- experts-exchange.com - Active Directory DFSR Sysvol - Authoritative and Non Authoritative Restore Sequence
- learn.microsoft.com - How to force authoritative and non-authoritative synchronization for DFSR
KB Change/Issue Log
yyyy/mm/dd - Title
Issue
N/A
Solution
N/A
KB Meta
| Page Includes | @9#bkmrk-callout-danger-NoResponsibilityDisclaimer-5wod5ufe |